404
Hunting the Sigfox
Wireless IoT Network Security10
min
Introduction: Sigfox & RF Basics
20
min
Protocol Analysis and Security
About Me
- Florian Euchner (Jeija)
- EE Student @ University of Stuttgart
/ Jeija
Alice the Cow and Bob the farmer
- Happy life
- Always outdoors
- Likes to roam
- Gets sick


Attaching Sensors to Alice
How??

 Range,
Range,  Cost,
Cost,  Power
Power
WiFi - Electromagnetic Spectrum
WiFi → UNB
Bandwith ~ Data Rate
"Broadband" = "Fast"
"Ultra Narrow Band" = "Slow"
Throughput (Europe)
Uplink
- 0-12 bytes @ 100bit/s
- max. 140 packets per day, DBPSK
Downlink
- 8 bytes @ 600 bit/s
- max. 4 packets per day, GFSK
- Forget IP, DNS, HTTP, ...
Multiple Access: ALOHA / FTDMA
Not just cows…
|
|
|
|||
|
|
|
|
|
|
|
|
|
BINGO!
Sigfox
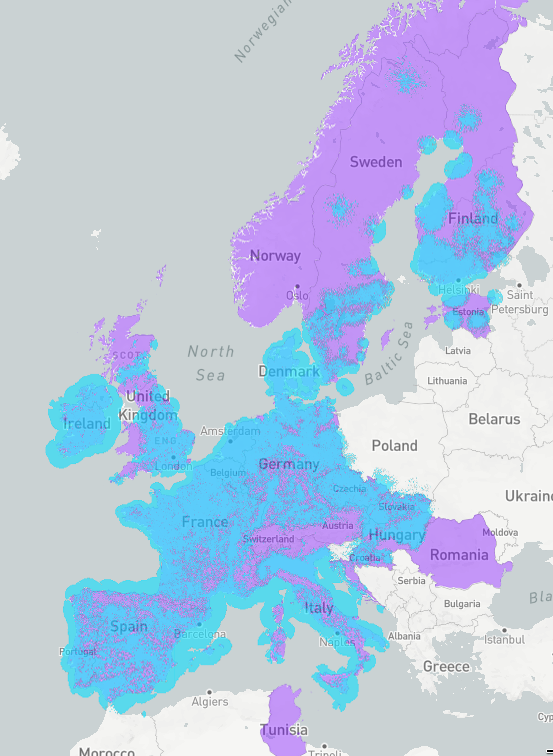
- French Startup
- Raised €250M+
- 3M - 6M Devices

- ~ 30km Range
- Years of Battery Life
- Unlicensed Spectrum (868 MHz)
- Proprietary
LPWAN Overview
LoRa
Sigfox
NB-IoT
Weightless-N
MIOTY
LTE-M
Telensa
ingenu RPMA
WAVIoT NB-Fi
DASH 7
RF Basics
Modulation
DBPSK
2-FSK
Uplink

Paul Pinault (disk91): The Sigfox radio protocol
https://disk91.com/2017/technology/sigfox/the-sigfox-radio-protocol/
Sniffing the uplink
Demodulating Sigfox Uplinks
D-BPSK (Phase Modulation)
Frames contents in hex
aaaaa06bc1a0db334d0069717b46
aaaaa6e09118806638c047959834
aaaaa034f1c8edff9e40732d2597
aaaaa06bc1a0db334d0069717b46
aaaaa6e09118806638c047959834
aaaaa034f1c8edff9e40732d2597
aaaaa06bc1a0db334d0069717b46
aaaaa6e09118806638c047959834
aaaaa034f1c8edff9e40732d2597
(5, 7) Convolutional Code
(5, 7) Convolutional Code
aaaaa06bc1a0db334d0069717b46
= decode(aaaaa6e09118806638c047959834, 5)
= decode(aaaaa034f1c8edff9e40732d2597, 7)
→ Error Correction, Coding Gain
(5, 7) Convolutional Code
aaaaa06bc1a0db334d0069717b46
= decode(aaaaa6e09118806638c047959834, 5)
= decode(aaaaa034f1c8edff9e40732d2597, 7)
→ Error Correction, Coding Gain
Capturing uncoded messages
Identifying Frame Fields
Payload: deadbeef16
aaaaa35f0a23db334d00deadbeef9a54ad20
aaaaa35f0a24db334d00deadbeef85845cad
aaaaa35f0a25db334d00deadbeef92387857
aaaaa35f0a26db334d00deadbeef77b69fac
spacer...
Identifying Frame Fields
Payload: deadbeef16
aaaaa35f0a23db334d00deadbeef9a54ad20
aaaaa35f0a24db334d00deadbeef85845cad
aaaaa35f0a25db334d00deadbeef92387857
aaaaa35f0a26db334d00deadbeef77b69fac
Preamble
Identifying Frame Fields
Payload: deadbeef16
aaaaa35f0a23db334d00deadbeef9a54ad20
aaaaa35f0a24db334d00deadbeef85845cad
aaaaa35f0a25db334d00deadbeef92387857
aaaaa35f0a26db334d00deadbeef77b69fac
Header
Identifying Frame Fields
Payload: deadbeef16
aaaaa35f0a23db334d00deadbeef9a54ad20
aaaaa35f0a24db334d00deadbeef85845cad
aaaaa35f0a25db334d00deadbeef92387857
aaaaa35f0a26db334d00deadbeef77b69fac
Sequence Number
Identifying Frame Fields
Payload: deadbeef16
aaaaa35f0a23db334d00deadbeef9a54ad20
aaaaa35f0a24db334d00deadbeef85845cad
aaaaa35f0a25db334d00deadbeef92387857
aaaaa35f0a26db334d00deadbeef77b69fac
Device ID (Unique)
Identifying Frame Fields
Payload: deadbeef16
aaaaa35f0a23db334d00deadbeef9a54ad20
aaaaa35f0a24db334d00deadbeef85845cad
aaaaa35f0a25db334d00deadbeef92387857
aaaaa35f0a26db334d00deadbeef77b69fac
Payload (Uncoded, Unencrypted)
Feature, not Bug

Sigfox Security Whitepaper
https://sigfox.com/en/technology/security
Uplink Frame Structure
F = Flags, SN = Sequence Number, L = Length Indication Bit, D = Downlink Request Bit
Uplink Frame Structure
F = Flags, SN = Sequence Number, L = Length Indication Bit, D = Downlink Request Bit
CRC-16
- 16 bit Cyclic Redundancy Check
- CRC-16-CCITT with negation
- Polynomial:
\[ 1021_{16} ~ \hat{=} ~ x^{16} + x^{12} + x^5 + 1 \]
→ Checksum (Random Transmission Errors)
Uplink Frame Structure
F = Flags, SN = Sequence Number, L = Length Indication Bit, D = Downlink Request Bit
Here:
Message Authentication Codes
≈ Digital Signature, but with symmetric schemeObtaining the Key
Can't be extracted
"This secret key is stored in a non-accessible memory…"

Security of the Sigfox Network (YouTube)
https://sigfox.com/en/technology/security
SiPy wants to "update firmware"...
SiPy Flash before FW update
003ff000: 70b3 d549 9a91 81ae ffff ffff ffff ffff p..I............
003ff010: ffff ffff ffff ffff ffff ffff ffff ffff ................
003ff020: ffff ffff ffff ffff ffff ffff ffff ffff ................
003ff030: ffff ffff ffff ffff ffff ffff ffff ffff ................
003ff040: ffff ffff ffff ffff ffff ffff ffff ffff ................
SiPy Flash after FW update
003ff000: 70b3 d549 9a91 81ae 004d 33db 4228 32b1 p..I.....M3.B(2.
003ff010: 5e7a 38d4 479e 4480 fd75 96d4 5b01 22fd ^z8.G.D..u..[.".
003ff020: 282d b3cf 0011 2233 4455 6677 8899 aabb (-...."3DUfw....
003ff030: ccdd eeff ffff ffff ffff ffff ffff ffff ................
003ff040: ffff ffff ffff ffff ffff ffff ffff ffff ................
SiPy Flash after FW update
003ff000: 70b3 d549 9a91 81ae 004d 33db 4228 32b1 p..I.....M3.B(2.
003ff010: 5e7a 38d4 479e 4480 fd75 96d4 5b01 22fd ^z8.G.D..u..[.".
003ff020: 282d b3cf 0011 2233 4455 6677 8899 aabb (-...."3DUfw....
003ff030: ccdd eeff ffff ffff ffff ffff ffff ffff ................
003ff040: ffff ffff ffff ffff ffff ffff ffff ffff ................
SiPy Flash after FW update
003ff000: 70b3 d549 9a91 81ae 004d 33db 4228 32b1 p..I.....M3.B(2.
003ff010: 5e7a 38d4 479e 4480 fd75 96d4 5b01 22fd ^z8.G.D..u..[.".
003ff020: 282d b3cf 0011 2233 4455 6677 8899 aabb (-...."3DUfw....
003ff030: ccdd eeff ffff ffff ffff ffff ffff ffff ................
003ff040: ffff ffff ffff ffff ffff ffff ffff ffff ................
SiPy Flash after FW update
003ff000: 70b3 d549 9a91 81ae 004d 33db 4228 32b1 p..I.....M3.B(2.
003ff010: 5e7a 38d4 479e 4480 fd75 96d4 5b01 22fd ^z8.G.D..u..[.".
003ff020: 282d b3cf 0011 2233 4455 6677 8899 aabb (-...."3DUfw....
003ff030: ccdd eeff ffff ffff ffff ffff ffff ffff ................
003ff040: ffff ffff ffff ffff ffff ffff ffff ffff ................
Me
Key is in plain in flash memory! What if someone gains physical access?
- We offer and recommend solutions, e.g. Secure Element chips
- Many device manufacturers don't use it
MAC Algorithm: CBC-MAC
Uplink Security
Me
Why no encryption?
- We offer an encrypted solution
- Many manufacturers don't use it
Uplink Security
\[
\bigg\}
\]
Brute-Force, Replay
 Brute Forcing
Brute Forcing
- Length: 2 - 5 Bytes
- 216 = 65536 possible values
\[ 2^{16} \cdot \mathsf{Uplink~Duration} < 4 \mathrm h \]
* = Single-Bit Uplink, RCZ2 (600bps)
Me
- Yes, but 16 bit is just worst case
- Device IDs will be blocked after too many attempts (exempt: development kits)
- A short
saves power
Me
Authenticity vs. Availability...
Replay
Replay
 = Replay Protection?
= Replay Protection?
Just 12 bits → 212 = 4096 
\[ \frac{2^{12} ~ \mathrm{SNs}}{140 ~ ^\mathrm{SNs}/_\mathrm{day}} < 30 ~ \mathrm{days} \]
Me
Sequence Number will overflow!
- Yes, but 30 days is worst case
- Encrypted solution extends SN to 20 bits
- Device manufacturers don't like it
Alice will be fine...
Smoke Detectors
Downlink
Uplink-initiated
Finding a base station


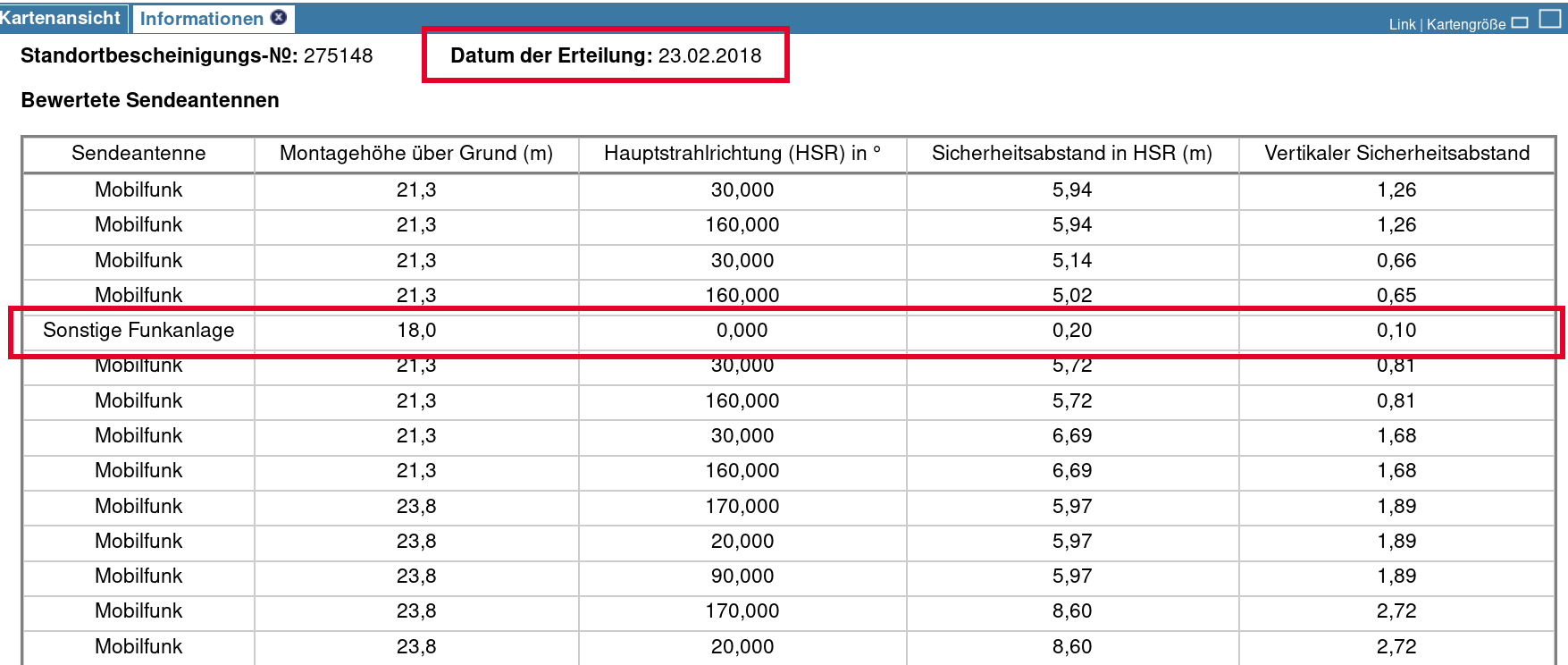 https://emf3.bundesnetzagentur.de
https://emf3.bundesnetzagentur.de
→ Dettingen unter Teck, Germany (48°36’49” N 9°26’43” E)
Demodulating Sigfox Downlinks
GFSK (Frequency Modulation)
Frame Contents in HEX
Identifying Frame Fields
Payload: 000000000000000016
2aaaaaaaaaaaaaaaaaaaaab2276d97647501fef287b35e9c10329658
2aaaaaaaaaaaaaaaaaaaaab227880a5d3855ad836e35740fb3d66ffa
2aaaaaaaaaaaaaaaaaaaaab22717b0ea9dced4a482e6f11efedd97fd
2aaaaaaaaaaaaaaaaaaaaab2271a9aae2a1b8ed4e2a4b17ccfa3562f
spacer...
Identifying Frame Fields
Payload: 000000000000000016
2aaaaaaaaaaaaaaaaaaaaab2276d97647501fef287b35e9c10329658
2aaaaaaaaaaaaaaaaaaaaab227880a5d3855ad836e35740fb3d66ffa
2aaaaaaaaaaaaaaaaaaaaab22717b0ea9dced4a482e6f11efedd97fd
2aaaaaaaaaaaaaaaaaaaaab2271a9aae2a1b8ed4e2a4b17ccfa3562f
Preamble
Identifying Frame Fields
Payload: 000000000000000016
2aaaaaaaaaaaaaaaaaaaaab2276d97647501fef287b35e9c10329658
2aaaaaaaaaaaaaaaaaaaaab227880a5d3855ad836e35740fb3d66ffa
2aaaaaaaaaaaaaaaaaaaaab22717b0ea9dced4a482e6f11efedd97fd
2aaaaaaaaaaaaaaaaaaaaab2271a9aae2a1b8ed4e2a4b17ccfa3562f
- Encryption?
- Error Correction Codes?
Scrambling
Inputs: Sequence Number + Device ID
 Well-established algorithms (CBC-MAC, AES)
Well-established algorithms (CBC-MAC, AES)
 No obvious implementation flaws
No obvious implementation flaws
 Scrambling ↛ Confidentiality
Scrambling ↛ Confidentiality
 Felix Fellhauer
Felix Fellhauer
 Marc Gauger
Marc Gauger
 Paul Pinault
Paul Pinault
 Alex Lehmann
Alex Lehmann
 Linus Neumann
Linus Neumann
 No major issues found
No major issues found






 jeija@jeija.net
jeija@jeija.net
 JEIJ (5345)
JEIJ (5345)
 ID: 004d33db, Key: 479e4480fd7596d45b0122fd282db3cf
ID: 004d33db, Key: 479e4480fd7596d45b0122fd282db3cf
Downlink Frame Structure
- BCH(15, 11, 1) Error Correction
- Message Authentication Code
Downlink Security
Solved by Sigfox's encrypted solution (P. Pinault)
Recommendations - For Developers
Do use Sigfox, but be aware of level of security- Buy one of the (still few) devices that support encryption
or
- Implement encryption on App layer if needed
- Uplink authenticity protection depends on payload length:
- 9 / 5 Bytes are most secure (40-bit MAC)
- 1 bit, 1 / 4 / 8 / 12 Bytes are least secure (16-bit MAC)
- Implement custom authenticity checks
Acknowledgements
 Felix Fellhauer
Felix Fellhauer
 Marc Gauger
Marc Gauger
 Paul Pinault
Paul Pinault
- Emojis: Twemoji, CC-BY 4.0
- Animations: Created with JS + CSS +
/3b1b/manim
- Drawings: CC-BY-SA 4.0 Florian Euchner (Jeija)
Acknowledgements
 Linus Neumann
Linus Neumann
- Emojis: Twemoji, CC-BY 4.0
- Animations: Created with JS + CSS +
/3b1b/manim
- Drawings: CC-BY-SA 4.0 Florian Euchner (Jeija)
Me
-
Our long-term goal is to open source the device protocol library
Me
Protocol Spec
renard-specC Library
librenardCLI Tool
renardSDR Implementation
renard-phyjeija.net/sigfox